Malware has traditionally been easy to spot and classify, mainly because it was created to serve a specific nefarious purpose and nothing else. In the ongoing arms race between malware authors and the security industry, stealth and other ‘in plain sight‘ technologies are emerging as clear favorites.
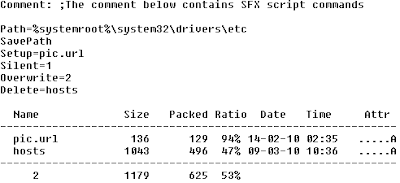
Case in point is a recent Craigslist phish, disguised as a phone update – nothing new about malware pretending to be something it isn’t, but that’s not where the story ends. Examining the executable shows that it is nothing more than a RAR self-extracting (SFX) archive – and thus not inherently malicious.
Contained within the archive are two seemingly innocent files; a HOSTS file and an internet shortcut (.url file). The internet shortcut points to craigslist and draws little or no suspicion when the object is scanned in isolation. The HOSTS file likewise contains mappings for various craigslist sub-domains, but without prior knowledge of the state of the HOSTS file, or dynamic resolution of the domains it is difficult to determine whether the mappings are legitimate (especially so when considered in isolation.)
When deployed as a complete package however, the HOSTS file remaps craigslist to some other IP so that when the internet shortcut is launched it goes to somewhere other than stated destination…in this case, a craigslist phish requesting login information.
So is it malware? Are any of the components malware? Clearly when these benign components are found acting in unison, malicious behavior is observed, but what about detection?
Traditional signature-based malware detection is obviously incapable of dealing with such multi-component threats, requiring instead a wider context-based observe-correlate-classify approach which draws from a variety of information sources such as reputation, nearest neighbour and behavior.
Because matches dont start fires, people do!