In Additional to my last post: http://boelectronic.blogspot.com/2010/03/twitter-phished-its-easy-mistake.html
We’ve received some questions regarding recent phishing attacks conducted against Twitter.com.
Tweets and Direct Messages (DM) containing phases such as “This you??” or “LOL is this you” are linking victims towards a Twitter login phishing page. If the bait is taken and victim enters their password, Twitter’s infamous “fail whale” is displayed and the user is returned to their account. They might not even realize that their account details have been compromised.
Phishing attacks directed against Twitter are not new. But what’s the point?
Trust.
Peers within a social network have a greater level of trust amongst themselves.
And so why the recent attacks?
We think it could have something to do with some of the recent search engine deals that have been made.
Yahoo announced that they’ll begin to include Twitter’s real-time feed into their search results and Facebook isnow included in Google’s search results.
The bad guys can use social networking trust to enhance their SEO attacks.
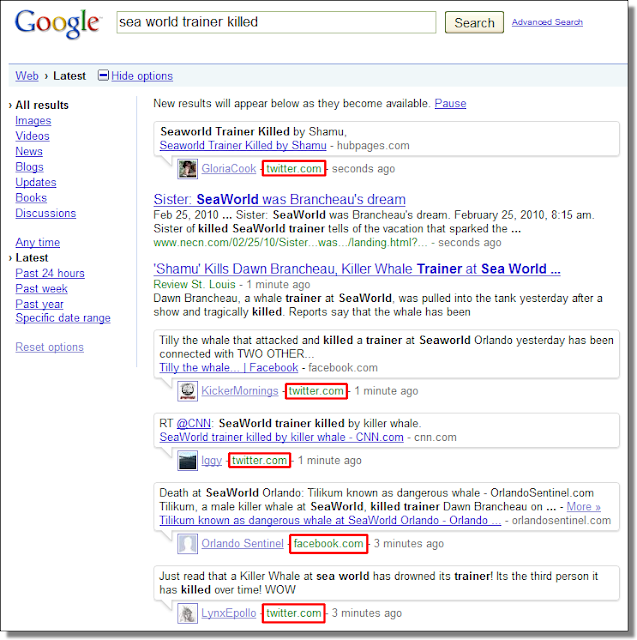
Lets take a current hot topic as an example. There are several Twitter results in the image below.
Note: Always be careful when searching for hot topics. This “sea world trainer killed” example is currently being used in SEO attacks and many results will lead directly to scamware.
There’s also a Facebook result in the example above. We expect to see fresh phishing attacks against Facebook before too long.
Twitter’s Safety and Spam feeds are useful to follow if you have a Twitter account. Twitter’s working on the issue now by prompting those that received phishing messages to change their password.
There is a silver lining to all of this…
While social networking trust can be abused, social networks themselves are incredibly responsive to emerging threats.
Check out the latest search results for “This you??“. Twitter users are already spreading information to counter the dis-information pushed by the bad guys.
It used to take weeks to stamp out e-mail hoaxes. Now, the issue almost corrects itself as quickly as it is abused.