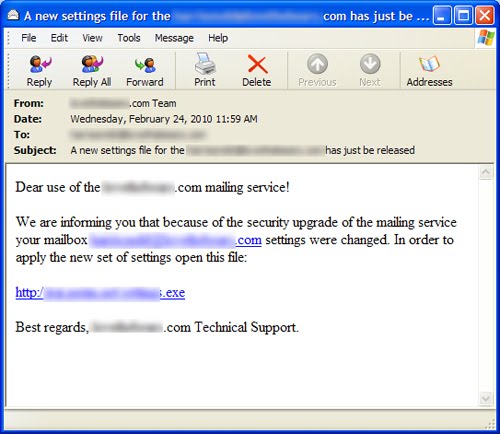
Imagine that you’re sitting at home catching up on your email backlog. In comes an email from your ISP, FooBarBazCo (some creativity required here, I know). The email seems to be from Technical Support – ‘From: FooBarBazCo.com Team’ – and states that you need to update your email settings as a result of a recent security upgrade. Can you trust it?
Today we observed an increase in spam messages containing links to a particular malicious URL. The messages masquerade as having come from mail administrators, with the ‘from’ address spoofed so that they appear to have come from the same network domain as the address to which the mails are sent (the ‘from’ and ‘to’ addresses are actually identical, although this will not be visible in most email programs).
The received messages state that mailbox ‘settings were changed’ and urge users to ‘apply the new set of settings’ by clicking a link to an executable, which unsurprisingly turns out to be malicious:
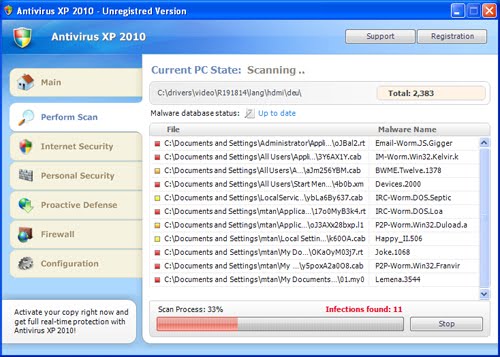
Clicking the link leads to a download of the following misleading application, which we see here with the usual UI misspellings and fake scan results:
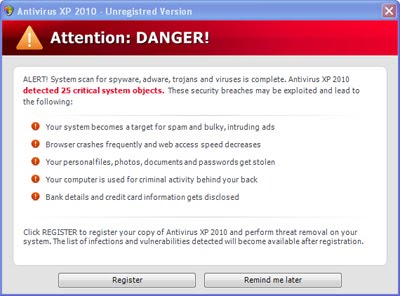
And, naturally, the usual prompt for registration:
Uh-oh: “25 critical system objects”! But I just installed the OS!
Symantec products detect the downloaded misleading application as AntiVirus2010. Do always be sure, however, to confirm with your ISP or IT team before following such “directions” to run a particular file and certainly before running any unknown executables hosted on external domains.